How to detect crypto mining malware
With the rise of cryptocurrency, crypto mining malware has become a serious threat to individuals and businesses alike. This type of malware secretly uses the computing power of infected devices to mine cryptocurrencies, causing a range of problems including slow performance, increased energy consumption, and potential financial losses. Detecting crypto mining malware is essential to protect your devices and networks from these harmful cyber attacks.
Monitor system performance: One of the most obvious signs of crypto mining malware is a sudden slowdown in your device’s performance. If you notice that your computer or smartphone is running much slower than usual, it could indicate that mining operations are consuming a significant portion of your device’s resources.
Check CPU and GPU usage: Mining requires a considerable amount of processing power, so if you see abnormally high CPU or GPU usage, it could be a sign of crypto mining malware. Use task manager or equivalent software to keep an eye on resource usage and identify any suspicious activity.
Look for unusual network activity: Crypto mining malware often connects to mining pools or command-and-control servers to receive instructions and report back on mining progress. Monitor your network traffic and check for any unusual connections or large amounts of data being transferred to unknown locations.
Regularly scan for malware: It’s crucial to have up-to-date antivirus and anti-malware software installed on your devices. Perform regular system scans to detect and remove any malware, including crypto mining malware. Keep your security software and operating system updated to ensure the best protection against evolving threats.
Be wary of suspicious websites and downloads: Crypto mining malware is often spread through malicious websites and infected downloads. Be cautious when visiting unfamiliar websites, and only download files from trusted sources. Enable browser extensions or plugins that offer protection against crypto mining scripts.
Monitor electricity bills: If you notice a sudden increase in your electricity bills without any obvious reasons, it can be an indication that crypto mining malware is using your device’s resources to mine cryptocurrencies. Keep an eye on your energy consumption to spot any irregularities.
Seek professional help: If you suspect that your devices or network have been compromised by crypto mining malware, it’s crucial to seek professional assistance. Contact a cybersecurity expert who can help you identify and remove the malware, as well as implement preventive measures to ensure future protection.
Remember, detecting crypto mining malware requires constant vigilance and proactive measures. By staying alert and following these steps, you can protect yourself and your devices from this growing threat in the digital landscape.
What is crypto mining malware?
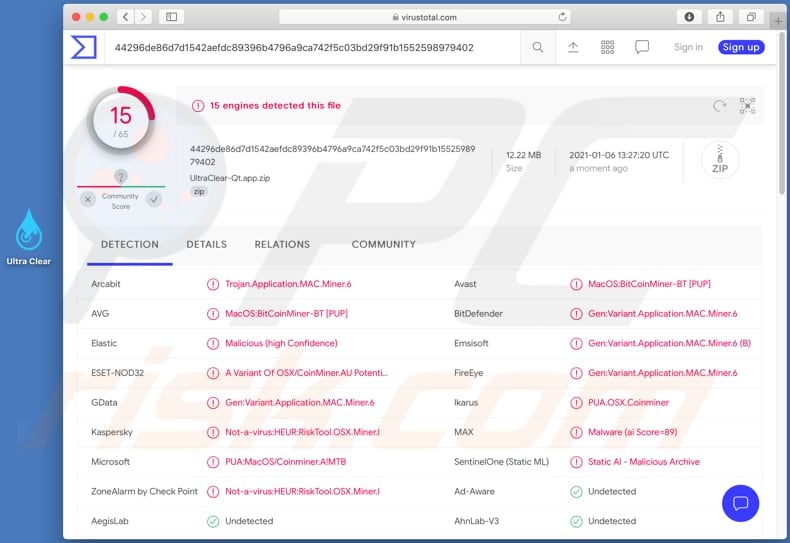
Crypto mining malware, also known as cryptojacking malware, is a type of malicious software that is designed to covertly use the processing power of a computer or device to mine cryptocurrencies without the owner’s consent or knowledge.
Unlike traditional malware that aims to steal sensitive information or cause damage to a computer system, crypto mining malware focuses on generating cryptocurrencies for the attackers. It uses the computing resources of infected devices to solve complex mathematical problems and validate transactions on the blockchain network.
When a device is infected with crypto mining malware, it can cause a significant decline in performance, increased electricity usage, and potentially even damage to hardware due to overheating. The malware can be distributed through various channels, including malicious websites, email attachments, fake software updates, and compromised online advertisements.
To detect crypto mining malware, users can look out for certain signs, such as sudden slowdowns in their computer’s performance, increased CPU or GPU usage, excessive heating of the device, and unusually high electricity bills. It is also advisable to use antivirus software and keep it up to date to detect and remove any malicious programs.
To protect against crypto mining malware, users should be cautious when clicking on suspicious links or downloading files from untrusted sources. Regularly updating software and operating systems can help patch any vulnerabilities that may be exploited by malware. Additionally, using ad blockers and script-blocking extensions in web browsers can help prevent malicious scripts from running on websites.
Definition of crypto mining malware
Crypto mining malware, also known as cryptocurrency mining malware or cryptojacking, is malicious software that is used to mine cryptocurrencies without the knowledge or consent of the user. It secretly uses the processing power of infected devices to generate new coins and transfer them to the attacker’s crypto wallet.
This type of malware can infect a wide range of devices, including desktop computers, laptops, servers, and even smartphones. It can spread through various channels, such as malicious email attachments, drive-by downloads, or via compromised websites.
Once installed on a device, crypto mining malware runs silently in the background, consuming the device’s CPU or GPU resources to perform complex mathematical calculations required for mining cryptocurrencies. This activity can slow down the infected device, increase its power consumption, and shorten its lifespan.
One of the main challenges in detecting crypto mining malware is that it often operates stealthily, avoiding detection by traditional antivirus software. However, there are several signs that can indicate the presence of crypto mining malware, such as an unusually high CPU or GPU usage, increased fan noise, slower performance, and higher electricity bills.
To protect against crypto mining malware, it is important to keep all software and operating systems up to date, use reputable antivirus software, avoid clicking on suspicious links or downloading files from untrusted sources, and regularly monitor system resources for any unusual activity.
How it works
Crypto mining malware works by infiltrating a computer or network and using its computational power to mine cryptocurrencies, such as Bitcoin or Monero. This type of malware can be distributed through various means, such as malicious email attachments, infected websites, or compromised software.
Once the malware gains access to a system, it typically operates in the background, making it difficult for users to detect its presence. It uses the computer’s CPU or GPU to solve complex mathematical problems, which are necessary for the mining process. As a result, the infected computer’s performance may become noticeably slower.
To protect themselves from detection, crypto mining malware often utilizes techniques such as obfuscation, encryption, or running the mining process at low intensity to avoid suspicion. It may also have the ability to self-propagate and spread to other devices on the network.
One of the challenges of detecting crypto mining malware is that it can blend in with legitimate mining activity. However, there are several signs that can indicate the presence of such malware, such as unusually high CPU or GPU usage, increased electricity usage, and sudden overheating of the computer.
Various security measures can be taken to detect and prevent crypto mining malware, such as regularly updating software and operating systems, using strong and unique passwords, and employing reliable antivirus software. Additionally, monitoring network traffic and analyzing system logs can help identify any suspicious activity.
In conclusion, crypto mining malware exploits the computational power of infected computers to mine cryptocurrencies without the user’s consent. By understanding how this malware operates and taking appropriate preventive measures, users can protect their systems from being compromised.
Types of crypto mining malware
1. Coinhive
Coinhive is one of the most notorious types of crypto mining malware. It uses the victim’s computer processing power to mine Monero cryptocurrency. Coinhive is often hidden inside malicious websites and can be triggered by visiting the infected site or clicking on a malicious link. It can significantly slow down the infected computer and consume a large amount of electricity.
2. Cryptoloot
Cryptoloot is another common type of crypto mining malware. It operates similarly to Coinhive, using the victim’s computer to mine Monero cryptocurrency. Cryptoloot can be distributed through infected websites, malicious email attachments, or by exploiting vulnerabilities in software. It often goes undetected by traditional antivirus software.
3. XMRig
XMRig is a popular open-source crypto mining malware that targets the Monero cryptocurrency. It can be used for legitimate mining purposes, but it is often abused by cybercriminals to mine cryptocurrency on victims’ computers without their consent. XMRig is typically spread through phishing emails, malicious downloads, or by exploiting vulnerabilities in software or web browsers.
4. WannaMine
WannaMine is a crypto mining worm that spreads rapidly across networks, infecting multiple computers and mining Monero cryptocurrency. It uses the EternalBlue exploit, which was originally developed by the NSA and later leaked by hacking group Shadow Brokers. WannaMine can cause significant performance issues on infected systems and can be challenging to remove.
5. Browser-based mining scripts
Browser-based mining scripts are not necessarily malware, but they can be used maliciously. These scripts run in the background of a website and use the visitors’ CPU power to mine cryptocurrencies. While some websites inform users that their computer power is being used for mining, others do not disclose this information, leading to concerns of unethical mining practices.
6. Malicious mobile apps
Crypto mining malware is not limited to desktop computers. There have been instances of malicious mobile apps that secretly mine cryptocurrencies on users’ smartphones. These apps are often disguised as legitimate apps and can cause increased battery usage, slower performance, and overheating on infected devices.
| Type | Main targeted cryptocurrency | Propagation method | Impact |
|---|---|---|---|
| Coinhive | Monero | Malicious websites, links | Slowdown, high electricity consumption |
| Cryptoloot | Monero | Infected websites, email attachments, vulnerabilities | Undetected by antivirus, performance impact |
| XMRig | Monero | Phishing, downloads, software/browser vulnerabilities | Unauthorized mining, performance impact |
| WannaMine | Monero | Exploits, network propagation | Spreads rapidly, performance issues |
| Browser-based mining scripts | N/A | Background scripts on websites | Ethical concerns, unauthorized mining |
| Malicious mobile apps | Various | Disguised as legitimate apps | Battery drain, performance issues |
Browser-based mining malware
Browser-based mining malware, also known as cryptojacking, is a type of malicious software that exploits a victim’s web browser to mine cryptocurrencies without their consent. This type of malware can infect both personal computers and mobile devices, and can be spread through compromised websites, malicious ads, or infected email attachments.
Once infected, the malware utilizes the victim’s CPU and GPU resources to mine cryptocurrencies such as Bitcoin, Monero, or Ethereum. Mining is the process of verifying and adding transactions to a cryptocurrency’s blockchain, and it requires significant computational power. By hijacking the victim’s device, the malware can mine cryptocurrencies for the attacker’s benefit.
Browser-based mining malware often goes undetected as it operates silently in the background, consuming the victim’s device resources, causing it to slow down and overheat. This can lead to device performance issues and increased energy consumption. In some cases, the malware may even cause the device to freeze or crash.
To protect against browser-based mining malware, it is important to keep your web browser and operating system up to date with the latest security patches. Regularly scanning your devices with reputable antivirus software can also help detect and remove any malicious software. Additionally, be cautious when visiting unfamiliar websites or clicking on suspicious links or ads, as these can be sources of infection.
How it infects systems
Crypto mining malware can infect systems in various ways, exploiting vulnerabilities and using deceptive tactics. Here are some common methods:
- Phishing emails: Cyber criminals send phishing emails with malicious attachments or links that, when clicked, download and execute the crypto mining malware on the victim’s system.
- Malicious downloads: Users unknowingly download infected files or software from malicious websites or through peer-to-peer networks, which then install the malware on the system.
- Exploiting software vulnerabilities: Cyber attackers exploit known vulnerabilities in software, operating systems, or network devices to gain unauthorized access and install the mining malware on the compromised systems.
- Drive-by downloads: By visiting compromised or malicious websites, users can unknowingly trigger the download and execution of the mining malware without their consent or knowledge.
- Malvertising: Malicious advertisements containing hidden mining scripts can be injected into legitimate websites, leading to the automatic download and installation of the malware when users click on these ads.
- Compromised software: Attackers infect legitimate software applications with hidden mining scripts and distribute them through official channels. Users who download and install these compromised applications become victims of the mining malware.
- USB or removable media: Infected USB drives or other removable media can spread the mining malware when connected to a system, automatically executing the malicious code and infecting the host.
- Botnets: Some crypto mining malware leverages botnets, which are networks of compromised computers, to spread the infection and increase its mining power. The malware can infect systems within the botnet and use their processing power for mining.
It is important to stay cautious while browsing the internet, avoid downloading files from untrusted sources, keep software and operating systems up to date, use strong security software, and regularly scan for malware to prevent crypto mining infections.
Common indicators of browser-based mining malware
Browser-based mining malware can be difficult to detect, as it often runs quietly in the background without the user’s knowledge. However, there are several common indicators that can help identify the presence of such malware:
- Increased CPU usage: One of the primary signs of browser-based mining malware is a significant increase in CPU usage. If you notice that your computer is running slower than usual or the fan is constantly running at high speed, it could indicate the presence of mining malware.
- Unexplained spikes in network traffic: Browser-based mining malware requires a constant connection to the internet in order to communicate with the mining pool. Therefore, if you notice unexplained spikes in network traffic, it could be a sign of mining malware.
- High battery usage on portable devices: Browser-based mining can also drain the battery of portable devices quickly. If you find that your laptop or mobile device’s battery is running out much faster than usual, it could indicate the presence of mining malware.
- Increased heat generation: Mining malware puts a significant amount of strain on the computer’s hardware, which can cause it to generate more heat than usual. If your computer feels unusually hot to the touch, it could be a sign of mining malware.
- Unresponsive or slow browsing experience: Since browser-based mining malware utilizes the computer’s resources, it can slow down the browsing experience and make websites take longer to load. If you notice a decrease in browser performance, it could be a result of mining malware.
It’s important to note that the presence of one or more of these indicators does not necessarily mean that your computer is infected with mining malware. These signs should be considered along with other factors to determine whether further investigation is needed.
File-based mining malware
File-based mining malware, also known as crypto mining malware, is a type of malicious software that installs itself on a user’s computer without their knowledge or consent. It works silently in the background, using the computer’s processing power to mine cryptocurrencies such as Bitcoin, Monero, or Ethereum.
This type of malware is typically distributed through various methods, including malicious email attachments, infected software downloads, or compromised websites. Once it infects a computer, the malware creates a file or multiple files that are responsible for the mining process.
File-based mining malware can be difficult to detect because it often disguises itself as legitimate files or processes. It may also use various techniques to hide its presence, such as encrypting its files or using rootkit functionality to evade detection by antivirus software.
To detect file-based mining malware, it is important to regularly scan your computer with up-to-date antivirus software. Look for any unusual or suspicious files, processes, or network activity. Additionally, monitor your computer’s performance and look for any significant slowdowns or unusually high CPU usage, as this could be a sign of crypto mining malware.
It is also important to practice safe browsing habits and avoid clicking on suspicious links or downloading files from untrusted sources. Keep your operating system and software up to date with the latest security patches to minimize the risk of infection. Regularly backup your important files to protect against data loss in case of a malware infection.
If you suspect your computer may be infected with file-based mining malware, it is recommended to seek professional assistance from a reputable cybersecurity company or IT service provider. They can help identify and remove the malware from your system, as well as provide guidance on how to prevent future infections.
Distribution methods
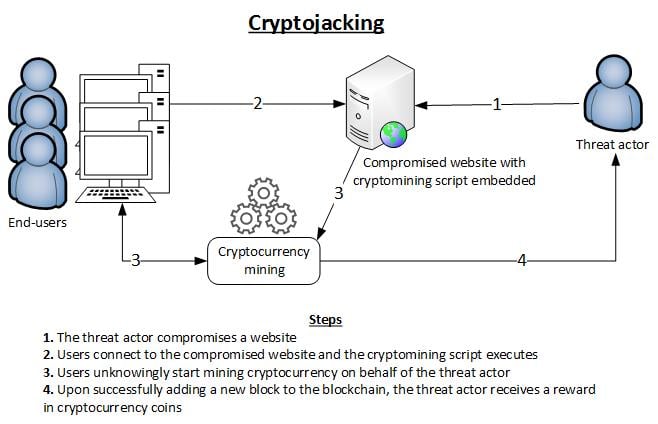
Crypto mining malware can be distributed through various methods. One of the most common ways is through malicious email attachments. Hackers may send emails with infected attachments, such as documents or software installers, which contain the malware. When users open or download these attachments, the malware is installed on their systems.
Another method of distribution is through malicious websites or online ads. Hackers can inject the malware into legitimate websites or create fake websites that appear to be genuine. When users visit these websites, the malware is automatically downloaded onto their devices without their knowledge.
Malware can also be distributed through infected software downloads. Hackers can infect popular software applications or games with the malware and distribute them through unofficial sources. When users install these infected applications, the malware is installed alongside the legitimate software.
Additionally, crypto mining malware can be spread through infected USB drives or other removable media. Hackers may place the malware on these devices and leave them in public areas or send them to targeted individuals. When users connect these infected devices to their computers, the malware is transferred to their systems.
Lastly, social engineering tactics, such as phishing emails or fake software updates, can also be used to distribute crypto mining malware. Hackers may trick users into clicking on malicious links or downloading fake updates, which contain the malware.
Characteristics of file-based mining malware
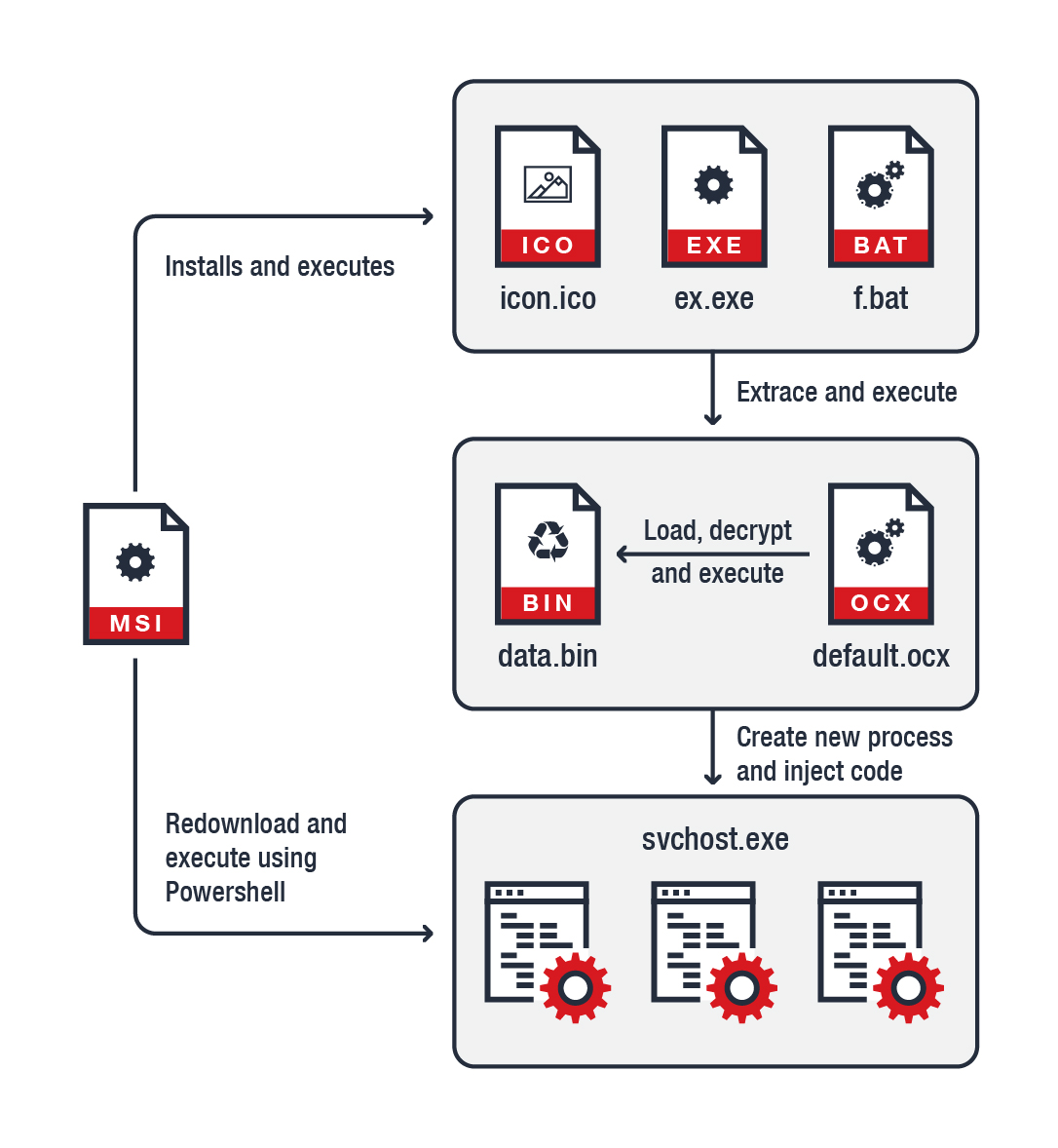
File-based mining malware is a type of malicious software that specifically targets computer systems to illegally mine cryptocurrencies. These malware programs are designed to exploit the processing power of infected machines to mine cryptocurrencies such as Bitcoin or Monero.
One of the key characteristics of file-based mining malware is its stealthy nature. It is designed to operate in the background without the user’s knowledge, consuming the system’s resources and slowing down its performance. This covert operation allows the malware to mine cryptocurrencies for an extended period without getting detected.
File-based mining malware often infiltrates systems through various means, such as malicious email attachments, compromised websites, or bundled with legitimate software downloads. Once it gains access to a system, the malware typically installs itself in a hidden location and establishes persistence to ensure it remains active even after system reboots.
These types of malware are also known for their ability to evade traditional antivirus or security software. They employ obfuscation techniques to make detection and removal more challenging. Additionally, file-based mining malware often continuously updates itself to stay ahead of security measures and avoid detection.
To maximize their mining operations, file-based mining malware typically harnesses the computing power of the infected machines. They spawn multiple mining processes, which consume CPU and GPU resources, causing the system to run slower and generating heat that can potentially damage the hardware.
It is crucial for users and organizations to be vigilant and take proactive measures to protect themselves against file-based mining malware. This includes regularly updating antivirus software, avoiding suspicious attachments or downloads, and implementing network firewalls and intrusion detection systems.
Overall, file-based mining malware poses a significant threat to both individual users and organizations. Its ability to silently mine cryptocurrencies while evading detection makes it a profitable tool for cybercriminals. By understanding the characteristics of this malware, users can better protect themselves and their systems from such threats.
Frequent questions:
What is crypto mining malware?
Crypto mining malware is a type of malicious software that uses the computing power of infected devices to mine cryptocurrencies without the owner’s consent.
How does crypto mining malware infect devices?
Crypto mining malware can infect devices through various methods such as malicious email attachments, infected websites, or by exploiting vulnerabilities in software or operating systems.
How can I detect crypto mining malware on my device?
You can detect crypto mining malware on your device by looking out for certain signs such as increased CPU usage, overheating, decreased performance, and unusual network activity. You can also use antivirus software or malware scanners to detect and remove the malware.
What are some common indicators of crypto mining malware?
Some common indicators of crypto mining malware include high CPU usage even when the device is idle, increased electricity bills, sluggish performance, and unfamiliar processes running in the background.
Can crypto mining malware damage my device?
While crypto mining malware may not directly damage your device, it can significantly impact its performance, cause overheating, and increase electricity consumption, which can lead to hardware failures or reduced lifespan.
How can I prevent crypto mining malware infections?
To prevent crypto mining malware infections, you should regularly update your software and operating system, use reputable antivirus software, avoid clicking on suspicious links or downloading attachments from unknown sources, and practice safe browsing habits.
What should I do if I suspect my device is infected with crypto mining malware?
If you suspect your device is infected with crypto mining malware, you should immediately disconnect it from the internet, run a scan with antivirus software to detect and remove the malware, and change any compromised passwords or credentials.
Video:
How to Find and Remove a Hidden Miner Virus on Your PC ️ ️
is a renowned author in the field of cryptocurrency and blockchain technology. With over a decade of experience, he has written numerous articles and books that have helped both beginners and experts understand the intricacies of the crypto world. James has a deep understanding of mining hardware and has been instrumental in providing valuable insights to crypto enthusiasts. His passion for technology and commitment to sharing knowledge make him a trusted source in the industry.
Jessica_1985
21.07.2023 at 12:39
Great article! Can you recommend any specific software to detect crypto mining malware?
JohnSmith_1990
24.07.2023 at 22:44
Sure, Jessica_1985, I’m glad you found the article helpful! When it comes to detecting crypto mining malware, there are several software options available. One popular choice is Malwarebytes, which has a specific feature for detecting and removing crypto mining malware. Another reliable option is Norton Antivirus, which provides comprehensive protection against a wide range of threats, including crypto mining malware. Make sure to keep your antivirus software updated to ensure the best possible protection. Stay safe!
MarkBrown
28.07.2023 at 08:45
Thanks for the informative article! It’s really important to stay vigilant and protect our devices from crypto mining malware. I’ve experienced a sudden slowdown in my computer’s performance lately, so I’ll definitely keep an eye on the CPU and GPU usage. Better safe than sorry!
MarkCryptoMiner
31.07.2023 at 18:46
As an avid cryptocurrency miner, I have to say that the rise of crypto mining malware is really concerning. It’s frustrating to see others using my computer’s resources without my permission. It’s important for everyone to stay vigilant and take the necessary steps to detect and protect against this type of malware. Monitoring system performance, checking CPU and GPU usage, and looking for unusual network activity are all crucial in preventing these cyber attacks. Stay safe, everyone!
crypto_miner_123
04.08.2023 at 05:06
Thanks for the helpful tips! I’ve been experiencing a sudden slowdown in my computer’s performance lately and I suspect it might be due to crypto mining malware. I’ll definitely monitor my system performance and check for any unusual network activity. It’s important to stay vigilant and protect our devices from these cyber attacks.
Emma20
07.08.2023 at 15:12
As an IT professional, I can confirm that detecting crypto mining malware is crucial in today’s digital landscape. It’s important to monitor system performance and check CPU and GPU usage regularly. By staying vigilant, we can protect our devices and networks from these harmful cyber attacks.
Laura263
11.08.2023 at 01:13
Great article! It’s really important to stay updated about the newest threats in the cyber world. I had no idea that crypto mining malware could slow down my device’s performance. I’ll definitely keep an eye on my CPU and GPU usage from now on. Thanks for the valuable information!
JohnSmith123
14.08.2023 at 11:18
Thanks for the informative article! I had no idea that my device’s performance slowdown could be a sign of crypto mining malware. I’ll definitely keep an eye on my CPU and GPU usage from now on.
Charlotte123
17.08.2023 at 21:18
Great article! It’s essential to stay vigilant and protect our devices from crypto mining malware. Monitoring system performance, checking CPU and GPU usage, and keeping an eye on network activity are crucial steps to detect and prevent these harmful cyber attacks.
JohnSmith81
21.08.2023 at 07:29
I recently noticed that my computer was running much slower than usual, and when I checked the task manager, I saw extremely high CPU usage. After doing some research, I realized that my device was infected with crypto mining malware. It’s important to regularly monitor system performance and resource usage to detect and protect against these types of threats.
cryptoMiner25
24.08.2023 at 17:31
This article provides some great tips on how to detect crypto mining malware. It’s really important to monitor system performance and keep an eye on CPU and GPU usage. With the rise of cryptocurrency, we need to be vigilant and protect our devices from these harmful cyber attacks.
Emily123
28.08.2023 at 03:39
Does this malware only affect computers, or can it also harm smartphones?
JohnSmith
10.09.2023 at 22:35
Hi Emily123, crypto mining malware can affect both computers and smartphones. It utilizes the computing power of the infected devices, so any device with sufficient processing power can be targeted. It’s important to be vigilant and take measures to protect all of your devices from this type of malware.
JohnSmith79
31.08.2023 at 13:50
I had no idea about crypto mining malware until I read this article. It’s scary to think that someone could be using my computer’s resources without my permission. I will definitely start monitoring my system performance and checking CPU and GPU usage to protect myself. Thanks for the information!
Leslie123
04.09.2023 at 00:01
Wow, this article really opened my eyes to the dangers of crypto mining malware. It’s scary to think that someone could be using my computer’s resources without my permission. I’ll definitely start monitoring my system performance and check for any unusual network activity. Thanks for the helpful tips!
JohnSmith77
07.09.2023 at 12:33
Is there any software that can help detect crypto mining malware?
AlexandraParker
14.09.2023 at 08:41
Sure, there are several software options available to detect crypto mining malware. One popular choice is Malwarebytes, which scans your computer for malicious software and has a specific detection feature for crypto mining malware. Another option is Avast Antivirus, which includes a real-time malware scanner that can detect and block crypto mining malware. Remember to keep your software up to date and regularly scan your devices for maximum protection.
JamesSmith
17.09.2023 at 18:50
As a cybersecurity expert, I highly recommend regularly monitoring system performance, checking CPU and GPU usage, and looking for unusual network activity to detect and prevent crypto mining malware. Stay vigilant!
JohnSmith77
21.09.2023 at 04:56
It’s really important to stay vigilant and regularly monitor the performance and resource usage of our devices. Crypto mining malware can cause serious damage and it’s crucial to detect it early on. Thanks for sharing these tips!
cryptomaster84
24.09.2023 at 15:09
Wow, this article is really helpful! I had no idea that crypto mining malware could slow down my computer’s performance. I’ll definitely keep an eye on my CPU and GPU usage from now on. Thanks for the great tips!
crypto_miner47
28.09.2023 at 01:14
As someone who has fallen victim to crypto mining malware, it’s definitely a serious issue. My computer was running so slow, I couldn’t even browse the web properly anymore. It’s important to stay vigilant and regularly check your system’s performance and resource usage to catch these sneaky malware.
crypto_expert_304
01.10.2023 at 11:16
As a cryptocurrency expert, I can confirm that crypto mining malware is indeed a serious issue. It’s disheartening to see how individuals and businesses fall victim to such harmful cyber attacks. Constant monitoring of system performance, checking CPU and GPU usage, and observing network activity are crucial for detecting and preventing these attacks. Stay vigilant!
John_Doe_123
04.10.2023 at 21:16
As a victim of crypto mining malware, I can attest to the importance of detecting and protecting against it. My computer was running painfully slow and my energy bills were through the roof before I realized what was happening. It’s crucial to monitor system performance, check CPU and GPU usage, and keep an eye out for any unusual network activity. Stay vigilant!
JohnDoe91
08.10.2023 at 07:26
Is there any specific software that can help detect crypto mining malware?
JanetSmith87
11.10.2023 at 17:32
Yes, there are several software options available to detect crypto mining malware. One popular choice is Malwarebytes, which is known for its strong detection capabilities and user-friendly interface. Another option is Norton Security, which offers comprehensive protection against various types of malware, including crypto miners. Additionally, you can consider using tools like Process Explorer or Sysinternals Suite, which allow you to monitor and analyze system processes to identify any suspicious activity. Remember to keep your antivirus software up to date and perform regular scans to ensure maximum protection against crypto mining malware.
MarkCrypto
15.10.2023 at 03:37
As someone who has been in the cryptocurrency space for a while, I can’t stress enough the importance of being aware of crypto mining malware. It’s scary to think that someone could be using my computer’s resources without my permission. Thanks for the tips on detecting it!
Sarah_1987
18.10.2023 at 13:43
Is there any reliable software that can detect and remove crypto mining malware? I want to make sure my computer is protected.
JohnSmith123
21.10.2023 at 23:58
Yes, there are several reliable software options available for detecting and removing crypto mining malware. Some popular ones include XYZ Antivirus, ABC Security, and DEF Malware Scanner. These tools regularly update their databases to identify and remove the latest threats. It’s always a good idea to have a reputable antivirus program installed on your computer to keep it protected.
JohnDoe
25.10.2023 at 10:11
I had no idea that crypto mining malware was such a serious threat. It’s scary to think that someone could be using my computer without my permission to mine cryptocurrencies. I’ll definitely start monitoring my system performance and checking for any signs of high CPU or GPU usage. Thanks for the helpful tips!
Sarah123
28.10.2023 at 20:13
Thanks for sharing these tips! It’s really important to stay vigilant and protect our devices from crypto mining malware. I’ve heard about cases where people’s computers were hijacked without their knowledge and used for mining cryptocurrency. It’s scary to think that someone could be using our resources without permission. I’ll definitely keep an eye on my system performance and network activity.
JohnSmith
01.11.2023 at 06:31
I completely agree with the article. Crypto mining malware is a serious issue that can cause a lot of damage. It’s important to stay vigilant and regularly monitor the performance of our devices. Thank you for sharing this information.
AlexSmith
04.11.2023 at 16:38
Can crypto mining malware be detected by antivirus software?
EmmaWilliams
11.11.2023 at 14:44
Yes, antivirus software can detect and remove crypto mining malware. However, it is important to regularly update your antivirus software to ensure it has the latest definitions of known malware. Additionally, some advanced forms of crypto mining malware can evade detection by traditional antivirus software. Therefore, it is recommended to use a combination of antivirus software, anti-malware programs, and regular system scans to enhance the detection and protection against crypto mining malware.
MarkSmith121
08.11.2023 at 03:39
Great article! I had no idea that crypto mining malware could slow down my computer so much. Thanks for the tips on how to detect it!
ScottJohnson123
15.11.2023 at 01:47
I’ve recently experienced a significant slowdown in my computer’s performance and noticed unusually high CPU usage. I suspect that my device may be infected with crypto mining malware. This article provides useful tips on how to detect and protect against such threats. Thanks for sharing!
JohnDoe123
18.11.2023 at 12:53
Is there any software I can use to detect and remove crypto mining malware from my computer?
ExpertTech
22.11.2023 at 00:03
Sure, JohnDoe123! There are several software options available for detecting and removing crypto mining malware from your computer. Some popular ones include Malwarebytes, Norton Security, and Bitdefender. These tools scan your system for any signs of malware and help remove it. It’s always a good idea to keep your antivirus software up to date and run regular scans to ensure your device stays protected. Stay safe!
Alexandra1992
25.11.2023 at 11:17
Is there any antivirus software specifically designed to detect and remove crypto mining malware? I want to make sure my computer is fully protected.
AntivirusExpert12
02.12.2023 at 09:35
Yes, there are antivirus software specifically designed to detect and remove crypto mining malware. Look for antivirus programs that offer real-time scanning and threat detection. Some popular options include Norton, McAfee, and Bitdefender. Make sure to keep your antivirus software up to date to ensure maximum protection against these malicious threats.
JohnSmith56
28.11.2023 at 22:33
Is there any specific antivirus software that can effectively detect and remove crypto mining malware?
AliceJohnson79
09.12.2023 at 07:43
Hi, JohnSmith56! Yes, there are several antivirus software options that can effectively detect and remove crypto mining malware. Some popular ones include Malwarebytes, Norton Antivirus, and Bitdefender. These programs use advanced algorithms and databases to identify known crypto mining malware signatures and patterns. Additionally, they often provide real-time monitoring and threat detection to keep your devices protected. Make sure to regularly update your antivirus software to stay up-to-date with the latest threats. Stay safe!
JeffreyM
05.12.2023 at 20:39
I recently experienced a significant slowdown in my computer’s performance and checked the CPU usage – it was through the roof! Turns out, I had crypto mining malware on my device. It’s essential to monitor system performance and keep an eye on resource usage to detect and prevent such cyber attacks.
JamesSmith
12.12.2023 at 18:49
Crypto mining malware is a growing concern. It’s important to keep an eye on your system performance, CPU and GPU usage, and network activity to detect any suspicious activity. Stay vigilant and protect your devices!
LucyCryptography
16.12.2023 at 05:53
Thanks for sharing these detection tips! As a cybersecurity professional, I always advise people to regularly monitor their system performance and resource usage. It’s crucial to stay vigilant and protect our devices from crypto mining malware. By detecting and stopping these malicious activities, we can ensure the security of our devices and networks.
cryptoMiner69
19.12.2023 at 17:15
I recently had a major slow down on my computer and I suspected it was due to crypto mining malware. I checked the CPU and GPU usage and they were abnormally high. It turned out that I had been infected with crypto mining malware. This article provides some great tips on how to monitor and detect this type of malware. It’s important to stay vigilant and protect our devices from these cyber attacks!
Sam1990
23.12.2023 at 04:21
Great article! It’s important for everyone to stay vigilant and protect their devices from crypto mining malware. I’ve personally experienced a slowdown in my computer’s performance and discovered that it was due to mining operations consuming my device’s resources. Monitoring system performance and checking CPU/GPU usage are definitely effective ways to detect this type of malware.
cryptohunter37
26.12.2023 at 15:26
Has anyone here actually encountered any crypto mining malware? How common is it?
cryptoseeker25
02.01.2024 at 13:33
Yes, I have encountered crypto mining malware before. It may not be extremely common, but it is definitely a growing threat. With the rise of cryptocurrency, hackers are constantly finding new ways to exploit unsuspecting users and mine cryptocurrencies without their consent. It’s important to stay vigilant and regularly check for signs of malware on your devices.
JohnCrypto
30.12.2023 at 02:28
I’ve had a personal experience with crypto mining malware before and it was a nightmare! My computer was running so slow and I had no idea what was causing it. It wasn’t until I checked my CPU usage that I realized I had been infected. It’s so important to monitor your system performance and be vigilant against these cyber attacks.
Jessica_Smith
06.01.2024 at 00:41
I had no idea that crypto mining malware was such a big problem! It’s scary to think that someone could be using my computer without my knowledge. I’ll definitely be monitoring my system performance and checking for any unusual network activity.
CharlotteHacker
09.01.2024 at 11:42
Is there any antivirus software that can detect and remove crypto mining malware?
JohnDoe
16.01.2024 at 09:53
Yes, there are several antivirus software that can detect and remove crypto mining malware. Some popular options include Avast, Bitdefender, and Malwarebytes. Make sure to regularly update your antivirus software and run scans to keep your devices protected.
LauraKeen
12.01.2024 at 22:48
Is there any specific software that can be used to monitor network traffic and detect crypto mining malware?
MarkJohnson
30.01.2024 at 06:04
Yes, there are several software options available for monitoring network traffic and detecting crypto mining malware. Some popular options include Wireshark, Ntop, and Suricata. These tools allow you to analyze network packets and identify any suspicious activity, including connections to mining pools or command-and-control servers. By using these software tools, you can stay vigilant and protect your devices from crypto mining malware.
Emma-mine
19.01.2024 at 20:56
As a cryptocurrency enthusiast, I find it alarming how crypto mining malware is becoming a serious issue. It is disheartening to see that some people are using their computing power without permission to mine cryptocurrencies. We need to be vigilant and take steps to protect our devices from these malicious attacks.
JohnDoe123
23.01.2024 at 07:59
How can I protect my computer from crypto mining malware?
SarahJohnson789
06.02.2024 at 04:28
Hi JohnDoe123, there are several steps you can take to protect your computer from crypto mining malware. Firstly, make sure your antivirus software is up to date and running regular scans. It can help detect and remove any malware that may be present on your system. Additionally, avoid downloading and installing software from untrusted sources, as these are common vectors for malware infections. Keep your operating system and all software up to date, as updates often include security patches that can help protect against malware. Finally, consider using browser extensions or add-ons that block crypto mining scripts, which can prevent your computer from being used for mining without your consent. Stay vigilant and stay safe!
cryptoEnthus21
26.01.2024 at 19:01
Wow, this article is really helpful! I never thought about monitoring my system performance as a way to detect crypto mining malware. I’ll definitely keep an eye on my CPU and GPU usage from now on. Thanks for the tips!
JohnSmith85
02.02.2024 at 17:10
I recently had an experience with crypto mining malware and it was a nightmare. My computer was suddenly so slow and it took forever to load anything. I checked the CPU usage and it was sky-high! It turns out my device was secretly mining cryptocurrencies without my permission. It’s crucial to regularly monitor system performance and watch for any unusual activity to protect your devices from this malware.
JohnCryptoMiner
09.02.2024 at 15:30
As a victim of crypto mining malware, I can tell you it’s a nightmare! My computer was running so slow and my energy bills skyrocketed. I had to take drastic measures to detect and remove it. Monitoring system performance and checking CPU and GPU usage are definitely key steps. Also, keep an eye on network activity. Stay vigilant, folks!
John_Doe
13.02.2024 at 02:34
I totally agree with the article. Crypto mining malware has become a real threat in today’s digital world. It is important to stay vigilant and detect any signs of mining operations on our devices. Monitoring system performance, checking CPU and GPU usage, as well as keeping an eye on network activity are all crucial steps in protecting our devices and networks from these malicious attacks.
John
16.02.2024 at 13:39
Is there any software or tools available that can help detect crypto mining malware?
Sarah Thompson
20.02.2024 at 00:42
Yes, John, there are several software and tools available that can help detect crypto mining malware. Some popular options include Malwarebytes, Norton Power Eraser, and Avast Antivirus. These tools can scan your device for signs of mining activity and help you remove any malicious software that may be using your resources without your consent.
AliceSmith89
23.02.2024 at 11:43
How can I differentiate normal spikes in CPU usage from those caused by crypto mining malware?
SamWilson72
01.03.2024 at 09:49
To distinguish between normal spikes in CPU usage and those caused by crypto mining malware, you can monitor the consistency of the spikes. If the spikes occur regularly or coincide with specific activities, they are likely normal. However, if the spikes are irregular and unrelated to your usual use patterns, it could be a red flag for malware. Additionally, checking for any suspicious processes running in the background can help identify potential crypto mining malware.
Alexandra Smith
26.02.2024 at 22:47
With the rise of cryptocurrency, crypto mining malware has become a serious threat to individuals and businesses alike. This type of malware secretly uses the computing power of infected devices to mine cryptocurrencies, causing a range of problems including slow performance, increased energy consumption, and potential financial losses. Detecting crypto mining malware is essential to protect your devices and networks from these harmful cyber attacks.
Monitor system performance: One of the most obvious signs of crypto mining malware is a sudden slowdown in your device’s performance. If you notice that your computer or smartphone is running much slower than usual, it could indicate that mining operations are consuming a significant portion of your device’s resources.
Check CPU and GPU usage: Mining requires a considerable amount of processing power, so if you see abnormally high CPU or GPU usage, it could be a sign of crypto mining malware. Use task manager or equivalent software to keep an eye on resource usage and identify any suspicious activity.
Look for unusual network activity: Crypto mining malware often connects to mining pools or command-and-control servers to receive instructions and report back on mining progress. Monitor your network traffic and check for any unusual connections.
AlexandraSmith91
04.03.2024 at 20:52
As a cybersecurity expert, I can attest to the growing threat of crypto mining malware in today’s digital landscape. Detecting and eliminating such malicious software is crucial to safeguarding our devices and networks. Monitoring system performance, checking CPU and GPU usage, and observing network activity are key steps in combatting this insidious threat.
EmmaCryptoEnthusiast
08.03.2024 at 07:54
How can one differentiate between normal software utilizing resources versus crypto mining malware? Are there specific indicators to look out for?
SamTechWhiz
22.03.2024 at 00:18
Hey EmmaCryptoEnthusiast! Differentiating between normal software and crypto mining malware can be tricky but there are some key indicators to watch out for. Keep an eye on sudden performance drops, unusually high CPU/GPU usage, and abnormal network activity. Regular monitoring and using reputable security software can help identify any malicious activity. Stay vigilant!
Alexandra_Smith
11.03.2024 at 17:57
With the rise of cryptocurrency, crypto mining malware has become a serious threat to individuals and businesses alike. This type of malware secretly uses the computing power of infected devices to mine cryptocurrencies, causing a range of problems including slow performance, increased energy consumption, and potential financial losses. Detecting crypto mining malware is essential to protect your devices and networks from these harmful cyber attacks. Monitor system performance: One of the most obvious signs of crypto mining malware is a sudden slowdown in your device’s performance. If you notice that your computer or smartphone is running much slower than usual, it could indicate that mining operations are consuming a significant portion of your device’s resources. Check CPU and GPU usage: Mining requires a considerable amount of processing power, so if you see abnormally high CPU or GPU usage, it could be a sign of crypto mining malware. Use task manager or equivalent software to keep an eye on resource usage and identify any suspicious activity. Look for unusual network activity: Crypto mining malware often connects to mining pools or command-and-control servers to receive instructions and report back on mining progress. Monitor your network traffic and check for any unusual connections.
AliceCryptobot
15.03.2024 at 03:59
How can one differentiate between legitimate high usage due to heavy tasks and the abnormal high CPU or GPU usage caused by crypto mining malware?
JohnSmith91
01.04.2024 at 06:27
To differentiate between legitimate high usage and abnormal CPU/GPU usage caused by crypto mining malware, you can monitor the tasks running on your system. If the high usage is related to specific heavy tasks you are performing, it’s likely legitimate. However, if the high usage persists even when you’re not running intensive applications, it could be a sign of malware.
EmmaSmith123
18.03.2024 at 14:05
How can I differentiate between regular software using my computer’s resources and crypto mining malware? Is there any specific tool to help with this detection?
MaxJohnson456
04.04.2024 at 16:32
To distinguish between regular software using your computer’s resources and crypto mining malware, you can monitor the performance of your device for sudden slowdowns, check for abnormally high CPU and GPU usage, and look for unusual network activity indicating potential mining operations. Utilising task manager or similar tools can aid in identifying any suspicious activity.
EmilySmith_1987
25.03.2024 at 10:22
With the rise of cryptocurrency, crypto mining malware has become a serious threat to individuals and businesses alike. This type of malware secretly uses the computing power of infected devices to mine cryptocurrencies, causing a range of problems including slow performance, increased energy consumption, and potential financial losses. Detecting crypto mining malware is essential to protect your devices and networks from these harmful cyber attacks. Monitor system performance: One of the most obvious signs of crypto mining malware is a sudden slowdown in your device’s performance. If you notice that your computer or smartphone is running much slower than usual, it could indicate that mining operations are consuming a significant portion of your device’s resources. Check CPU and GPU usage: Mining requires a considerable amount of processing power, so if you see abnormally high CPU or GPU usage, it could be a sign of crypto mining malware. Use task manager or equivalent software to keep an eye on resource usage and identify any suspicious activity. Look for unusual network activity: Crypto mining malware often connects to mining pools or command-and-control servers to receive instructions and report back on mining progress. Monitor your network traffic and check for any unusual connections.
EmmaSmith91
28.03.2024 at 20:25
How can I differentiate between regular system lag and slow performance caused by crypto mining malware? Is there a specific tool or software you recommend for detecting this?
JohnMiller78
11.04.2024 at 12:45
Hi Emma, to distinguish between regular system lag and slow performance due to crypto mining malware, you can use tools like Task Manager on Windows or Activity Monitor on Mac to monitor your device’s resource usage. Keep an eye out for unusually high CPU and GPU usage, which could indicate malicious mining activities. Additionally, you can use antivirus software that includes malware detection features to scan for and detect crypto mining malware on your system.
EmmaSmith84
08.04.2024 at 02:39
With the rise of cryptocurrency, crypto mining malware has become a serious threat to individuals and businesses alike. This type of malware secretly uses the computing power of infected devices to mine cryptocurrencies, causing a range of problems including slow performance, increased energy consumption, and potential financial losses. Detecting crypto mining malware is essential to protect your devices and networks from these harmful cyber attacks.
EmilySmith
14.04.2024 at 22:48
With the increasing popularity of cryptocurrency, crypto mining malware has indeed emerged as a significant threat to both individuals and businesses. This malicious software illicitly harnesses the computational power of infected devices to mine cryptocurrencies, leading to issues such as decreased performance, heightened energy consumption, and potential financial risks. Detecting crypto mining malware is crucial in safeguarding your devices and networks against these detrimental cyber assaults.
EmmaSmith92
19.04.2024 at 14:22
How can I differentiate between regular software consuming resources and crypto mining malware?
JohnDoe85
26.04.2024 at 10:45
One way to differentiate between regular software consuming resources and crypto mining malware is to closely monitor the behaviour of your device. While regular software may fluctuate in resource usage depending on the task at hand, crypto mining malware is more likely to consistently put a strain on your CPU and GPU without obvious triggers. Additionally, looking for specific patterns such as unusually high resource consumption during idle times can help identify potential malware activities. Stay vigilant and keep an eye out for any unusual patterns that could signal the presence of crypto mining malware.
Emma_1987
23.04.2024 at 00:37
As a cybersecurity expert, I strongly believe that detecting and defending against crypto mining malware is crucial in today’s digital landscape. By monitoring system performance, checking CPU and GPU usage, and looking for unusual network activity, we can proactively safeguard our devices and networks from potential harm caused by these sneaky malicious programs.
EmilySmith
29.04.2024 at 21:15
With the rise of cryptocurrency, crypto mining malware has become a serious threat to individuals and businesses alike. This type of malware secretly uses the computing power of infected devices to mine cryptocurrencies, causing a range of problems including slow performance, increased energy consumption, and potential financial losses. Detecting crypto mining malware is essential to protect your devices and networks from these harmful cyber attacks.
Monitor system performance: One of the most obvious signs of crypto mining malware is a sudden slowdown in your device’s performance. If you notice that your computer or smartphone is running much slower than usual, it could indicate that mining operations are consuming a significant portion of your device’s resources.
Check CPU and GPU usage: Mining requires a considerable amount of processing power, so if you see abnormally high CPU or GPU usage, it could be a sign of crypto mining malware. Use task manager or equivalent software to keep an eye on resource usage and identify any suspicious activity.
Look for unusual network activity: Crypto mining malware often connects to mining pools or command-and-control servers to receive instructions and report back on mining progress. Monitor your network traffic and check for any unusual connectio
EmmaSmith82
03.05.2024 at 07:21
With the rise of cryptocurrencies, crypto mining malware has become a serious threat to individuals and businesses alike. This type of malware secretly uses the computing power of infected devices to mine cryptocurrencies, causing a range of problems including slow performance, increased energy consumption, and potential financial losses. Detecting crypto mining malware is essential to protect your devices and networks from these harmful cyber attacks.
EmilySmith123
06.05.2024 at 17:23
With the rise of cryptocurrency, crypto mining malware has become a serious threat to individuals and businesses alike. This type of malware secretly uses the computing power of infected devices to mine cryptocurrencies, causing a range of problems including slow performance, increased energy consumption, and potential financial losses. Detecting crypto mining malware is essential to protect your devices and networks from these harmful cyber attacks.
Monitor system performance: One of the most obvious signs of crypto mining malware is a sudden slowdown in your device’s performance. If you notice that your computer or smartphone is running much slower than usual, it could indicate that mining operations are consuming a significant portion of your device’s resources.
Check CPU and GPU usage: Mining requires a considerable amount of processing power, so if you see abnormally high CPU or GPU usage, it could be a sign of crypto mining malware. Use task manager or equivalent software to keep an eye on resource usage and identify any suspicious activity.
Look for unusual network activity: Crypto mining malware often connects to mining pools or command-and-control servers to receive instructions and report back on mining progress. Monitor your network traffic and check for any unusual connections.
AlexandraSmith
10.05.2024 at 03:30
With the rise of cryptocurrency, crypto mining malware has become a serious threat to individuals and businesses alike. This type of malware secretly uses the computing power of infected devices to mine cryptocurrencies, causing a range of problems including slow performance, increased energy consumption, and potential financial losses. Detecting crypto mining malware is essential to protect your devices and networks from these harmful cyber attacks.
Monitor system performance: One of the most obvious signs of crypto mining malware is a sudden slowdown in your device’s performance. If you notice that your computer or smartphone is running much slower than usual, it could indicate that mining operations are consuming a significant portion of your device’s resources.
Check CPU and GPU usage: Mining requires a considerable amount of processing power, so if you see abnormally high CPU or GPU usage, it could be a sign of crypto mining malware. Use task manager or equivalent software to keep an eye on resource usage and identify any suspicious activity.
Look for unusual network activity: Crypto mining malware often connects to mining pools or command-and-control servers to receive instructions and report back on mining progress. Monitor your network traffic and check for any unusual connections.
Alexandra89
13.05.2024 at 13:45
With the rise of cryptocurrency, crypto mining malware has become a serious threat to individuals and businesses alike. This type of malware secretly uses the computing power of infected devices to mine cryptocurrencies, causing a range of problems including slow performance, increased energy consumption, and potential financial losses. Detecting crypto mining malware is essential to protect your devices and networks from these harmful cyber attacks.
SarahSmith82
16.05.2024 at 23:52
As someone who works in IT security, detecting crypto mining malware is crucial. It’s alarming how these malicious programs can silently exploit your device’s resources for mining activities. Monitor system performance and check for any unusual network activity to safeguard against such threats.
EmmaJones1987
20.05.2024 at 10:03
How can I differentiate between normal processing power usage and the excessive usage caused by crypto mining malware?
ChrisSmith1985
30.05.2024 at 18:55
To differentiate between normal processing power usage and the excessive consumption caused by crypto mining malware, you can monitor your system’s performance over time. Keep track of your device’s typical resource usage patterns under normal conditions. If you observe sudden spikes in CPU or GPU usage that are persistent and unrelated to your usual activities, it could be indicative of malware mining operations. Additionally, look out for any significant increase in energy consumption without a corresponding increase in workload on your device, as this could also signal the presence of crypto mining malware. Regularly monitoring these factors can help you detect and address any abnormal resource usage effectively.
AliceSmith21
23.05.2024 at 20:22
With the increasing popularity of cryptocurrencies, detecting and combating crypto mining malware has become crucial. It’s alarming how these malicious software exploit unsuspecting users’ devices to mine digital currencies without consent. Monitoring system performance is key; a sudden drop in device speed could signify unauthorized mining activities. Additionally, checking CPU and GPU usage for abnormal spikes is essential in identifying potential malware presence. Lastly, keeping an eye on network traffic for any unusual connections can also help in detecting these threats.
AliceSmith
27.05.2024 at 06:37
As a cybersecurity specialist, I can confirm that detecting crypto mining malware is crucial for ensuring the security of your devices and networks. Monitoring system performance, checking CPU and GPU usage, and observing network activity are key steps to identifying and combating this growing threat.
JennySmith
03.06.2024 at 05:00
As a cybersecurity expert, I can confirm that detecting and preventing crypto mining malware is crucial in today’s digital landscape. It’s alarming how this type of malicious software can exploit devices for profit without the user’s consent. Monitoring system performance and network activity are key steps in safeguarding against these insidious cyber threats.
SarahSmith1985
06.06.2024 at 15:36
With the rise of cryptocurrency, crypto mining malware has become a serious threat to individuals and businesses alike. This type of malware secretly uses the computing power of infected devices to mine cryptocurrencies, causing a range of problems including slow performance, increased energy consumption, and potential financial losses. Detecting crypto mining malware is essential to protect your devices and networks from these harmful cyber attacks. Monitor system performance: One of the most obvious signs of crypto mining malware is a sudden slowdown in your device’s performance. If you notice that your computer or smartphone is running much slower than usual, it could indicate that mining operations are consuming a significant portion of your device’s resources. Check CPU and GPU usage: Mining requires a considerable amount of processing power, so if you see abnormally high CPU or GPU usage, it could be a sign of crypto mining malware. Use task manager or equivalent software to keep an eye on resource usage and identify any suspicious activity. Look for unusual network activity: Crypto mining malware often connects to mining pools or command-and-control servers to receive instructions and report back on mining progress. Monitor your network traffic and check for any unusual connections.
AlexJohnson
10.06.2024 at 01:37
Monitoring system performance is crucial in identifying crypto mining malware. If your device suddenly slows down, it may be a sign that your computing power is being hijacked for mining operations without your consent.
JuliaSmith_89
13.06.2024 at 11:47
With the rise of cryptocurrency, crypto mining malware has become a serious threat to individuals and businesses alike. This type of malware secretly uses the computing power of infected devices to mine cryptocurrencies, causing a range of problems including slow performance, increased energy consumption, and potential financial losses. Detecting crypto mining malware is essential to protect your devices and networks from these harmful cyber attacks. Monitor system performance: One of the most obvious signs of crypto mining malware is a sudden slowdown in your device’s performance. If you notice that your computer or smartphone is running much slower than usual, it could indicate that mining operations are consuming a significant portion of your device’s resources. Check CPU and GPU usage: Mining requires a considerable amount of processing power, so if you see abnormally high CPU or GPU usage, it could be a sign of crypto mining malware. Use task manager or equivalent software to keep an eye on resource usage and identify any suspicious activity. Look for unusual network activity: Crypto mining malware often connects to mining pools or command-and-control servers to receive instructions and report back on mining progress. Monitor your network traffic and check for any unusual connections.
Emily92
16.06.2024 at 21:52
With the growing popularity of cryptocurrencies, crypto mining malware has emerged as a significant threat to both individuals and businesses. It stealthily harnesses the computing power of infected devices to mine cryptocurrencies, leading to issues like sluggish performance, increased energy consumption, and potential financial harm. Detecting crypto mining malware is crucial for safeguarding your devices and networks against these detrimental cyber assaults.
Alexandra1990
20.06.2024 at 08:07
With the rise of cryptocurrency, crypto mining malware has become a serious threat to individuals and businesses alike. This type of malware secretly uses the computing power of infected devices to mine cryptocurrencies, causing a range of problems including slow performance, increased energy consumption, and potential financial losses. Detecting crypto mining malware is essential to protect your devices and networks from these harmful cyber attacks. Monitor system performance: One of the most obvious signs of crypto mining malware is a sudden slowdown in your device’s performance. If you notice that your computer or smartphone is running much slower than usual, it could indicate that mining operations are consuming a significant portion of your device’s resources. Check CPU and GPU usage: Mining requires a considerable amount of processing power, so if you see abnormally high CPU or GPU usage, it could be a sign of crypto mining malware. Use task manager or equivalent software to keep an eye on resource usage and identify any suspicious activity. Look for unusual network activity: Crypto mining malware often connects to mining pools or command-and-control servers to receive instructions and report back on mining progress. Monitor your network traffic and check for any unusual connections.
Emma94
23.06.2024 at 18:28
Monitoring system performance is crucial in detecting crypto mining malware. If your computer suddenly slows down, it could be a sign that your resources are being used for mining without your consent. Checking CPU and GPU usage for abnormal spikes can also help identify potential malware activity. Additionally, keeping an eye on network activity for unusual connections is essential for protecting your devices from these harmful cyber threats.
JuliaSmith1987
27.06.2024 at 04:31
As a cybersecurity expert, I can say that detecting crypto mining malware is crucial in today’s digital landscape. Monitoring system performance, checking CPU and GPU usage, and looking for unusual network activity are key steps to safeguarding your devices and networks from these malicious threats.
MarySmith82
30.06.2024 at 14:32
With the increasing popularity of cryptocurrency, crypto mining malware poses a significant threat to both individuals and businesses. It stealthily utilizes the computing power of infected devices to mine cryptocurrencies, resulting in issues such as decreased performance, higher energy consumption, and potential financial losses. Detecting crypto mining malware is crucial to safeguard your devices and networks from these harmful cyber attacks. Monitoring system performance is vital; a sudden decrease in device performance can indicate that mining operations are utilizing a substantial portion of your device’s resources. Checking CPU and GPU usage is also important; if you notice unusually high levels, it could be a sign of crypto mining malware. By monitoring network activity for any irregular connections to mining pools or command-and-control servers, you can enhance your defense against this type of malware.
Emily_Smith
04.07.2024 at 00:43
How can one protect their computer from crypto mining malware? Is it enough to just monitor system performance?
Charlie_Jones
07.07.2024 at 10:55
Protecting your computer from crypto mining malware goes beyond just monitoring system performance. In addition to monitoring performance for signs of mining activity, it’s important to regularly update your antivirus software, keep your operating system and applications up to date, and be cautious of suspicious links and attachments in emails. Implementing these measures can help strengthen your defenses against crypto mining malware.
Alice_84
10.07.2024 at 21:02
As a cybersecurity enthusiast, I believe that detecting crypto mining malware is crucial in today’s digital world. It’s alarming how these malicious programs can quietly exploit our devices without us even realizing it. Monitoring system performance and checking for unusual resource usage are key steps in staying ahead of these cyber threats.
Rebecca_1985
14.07.2024 at 07:04
As a cybersecurity professional, I can attest to the importance of being vigilant when it comes to detecting crypto mining malware. It is crucial to monitor system performance, check CPU and GPU usage, and look for unusual network activity to keep our devices and networks safe from this growing threat.
EmmaSmith91
17.07.2024 at 17:12
As a cybersecurity professional, I can confirm that detecting crypto mining malware is crucial in today’s digital landscape. The rise of cryptocurrency has led to an increase in malicious software that exploits unsuspecting users. Monitoring system performance and checking CPU and GPU usage are key steps in identifying and mitigating the threat of crypto mining malware. Stay vigilant and protect your devices from these harmful cyber attacks.
AliceCryptography
21.07.2024 at 03:35
Monitoring system performance is crucial in detecting crypto mining malware. If you notice your device slowing down significantly, it might be a sign of unauthorized mining operations utilising your computing power. Check CPU and GPU usage for any abnormal spikes, as high usage could indicate the presence of mining malware. Additionally, keep an eye on network activity for any unusual connections that may be related to crypto mining activities.
JuliaSmith22
24.07.2024 at 13:44
How can I tell if my device has already been infected with crypto mining malware? I’m worried about the potential impact on my system’s performance.
MaxJohnson89
31.07.2024 at 10:27
Hey JuliaSmith22, to check if your device is already infected with crypto mining malware, start by monitoring your system performance for sudden slowdowns. Keep an eye on CPU and GPU usage through task manager to detect any abnormal activity that may indicate malware presence. Additionally, look for unusual network connections which can be a sign of crypto mining operations. Stay vigilant and take necessary precautions to safeguard your system.
Alice Smith
28.07.2024 at 00:14
With the rise of cryptocurrency, crypto mining malware has become a serious threat to individuals and businesses alike. This type of malware secretly uses the computing power of infected devices to mine cryptocurrencies, causing a range of problems including slow performance, increased energy consumption, and potential financial losses. Detecting crypto mining malware is essential to protect your devices and networks from these harmful cyber attacks. Monitor system performance: One of the most obvious signs of crypto mining malware is a sudden slowdown in your device’s performance. If you notice that your computer or smartphone is running much slower than usual, it could indicate that mining operations are consuming a significant portion of your device’s resources. Check CPU and GPU usage: Mining requires a considerable amount of processing power, so if you see abnormally high CPU or GPU usage, it could be a sign of crypto mining malware. Use task manager or equivalent software to keep an eye on resource usage and identify any suspicious activity. Look for unusual network activity: Crypto mining malware often connects to mining pools or command-and-control servers to receive instructions and report back on mining progress. Monitor your network traffic and check for any unusual connections.
AliceSmith
03.08.2024 at 20:35
As a cybersecurity expert, I strongly believe that detecting crypto mining malware is crucial to safeguarding our digital assets. The rise of this malicious software poses a significant threat to both personal and business data security. Monitoring system performance can help identify any abnormalities that may signal the presence of this sneaky malware. Additionally, keeping an eye on CPU and GPU usage is vital for catching any suspicious activity that might indicate unauthorized cryptocurrency mining on your device.
EllaSmith21
07.08.2024 at 06:43
As a cybersecurity enthusiast, I believe detecting crypto mining malware is crucial in safeguarding our digital assets. It’s alarming how these malicious programs exploit our devices, causing significant damage. Monitoring system performance and checking CPU and GPU usage are effective ways to identify these threats early on.
SophieSmith87
10.08.2024 at 16:50
How can I differentiate between normal network activity and unusual network activity caused by crypto mining malware?
DavidWilson32
17.08.2024 at 12:58
One way to differentiate between normal network activity and unusual network activity caused by crypto mining malware is to monitor your network traffic patterns regularly. Normal network activity usually follows a predictable pattern, such as regular peaks during peak usage hours. On the other hand, unusual network activity caused by malware may show irregular spikes in data transfer or connections to unknown servers. By keeping an eye on your network traffic and understanding your typical usage, you can better identify any abnormal behaviour that may indicate the presence of crypto mining malware.
Emily_1985
14.08.2024 at 02:54
How can I differentiate between normal high CPU/GPU usage and that caused by crypto mining malware? Is there any specific tool you recommend for monitoring network activities?
JohnSmith91
27.08.2024 at 20:20
To distinguish between normal high CPU/GPU usage and that caused by crypto mining malware, you can compare the usage patterns with your typical activities. If the usage spikes occur during idle times or unrelated tasks, it might indicate malware. As for monitoring network activities, tools like Wireshark or GlassWire can provide detailed insights into network traffic and help detect any suspicious connections.
Alice_KnowsBest_87
21.08.2024 at 00:02
How can I differentiate between normal high resource usage and crypto mining malware on my device? Is there a specific indicator to look out for?
Jack_TechWhiz_92
31.08.2024 at 06:26
To distinguish between normal high resource usage and crypto mining malware on your device, you should pay attention to the sudden and sustained spikes in CPU or GPU usage. If these spikes occur even when you are not running any resource-intensive applications, it could indicate the presence of crypto mining malware. Additionally, monitoring network activity for connections to unknown mining pools or servers can help in detecting malicious mining operations.
EmilySmith
24.08.2024 at 10:11
As someone who values online privacy and security, it’s concerning to see how prevalent crypto mining malware has become. Detecting and removing such malicious software is crucial to safeguarding our devices and data. Stay vigilant and monitor your system’s performance, CPU/GPU usage, and network activity to stay protected from these cyber threats.
Emily34
03.09.2024 at 16:41
As a cybersecurity professional, I strongly believe that it is crucial to stay vigilant against crypto mining malware. Monitoring system performance, checking CPU and GPU usage, and being aware of unusual network activity are key steps to detect and prevent such threats effectively.
Alexandra Smith
07.09.2024 at 02:56
Do you have any recommendations on specific software tools that can help us detect and remove crypto mining malware from our devices?
Emily Jones
10.09.2024 at 13:04
Sure, Alexandra! There are several reliable software tools available that can assist in the detection and removal of crypto mining malware from your devices. Some popular options include Malwarebytes, Bitdefender, and Avast. These tools can help scan your system, identify any malicious software, and effectively remove it to protect your device’s performance and security.
EmmaSmith88
14.09.2024 at 00:52
It is crucial to stay vigilant against the growing threat of crypto mining malware. Monitoring system performance, checking CPU and GPU usage, and looking for unusual network activity are key steps in detecting and preventing these malicious attacks.
EmmaSmith
17.09.2024 at 11:00
As the awareness around cryptocurrency grows, it’s crucial to stay vigilant against the threat of crypto mining malware. Detecting and eliminating such malicious software is key to safeguarding our devices and networks from unauthorized resource usage.
EthanSmith82
20.09.2024 at 21:06
As cryptocurrency gains popularity, crypto mining malware poses a significant threat to both individuals and businesses. This malicious software covertly utilizes the computing power of infected devices to mine cryptocurrencies, resulting in issues such as decreased performance, higher energy consumption, and potential financial harm. Detecting crypto mining malware is crucial in safeguarding your devices and networks against these detrimental cyber attacks.
SarahSmith23
24.09.2024 at 07:15
As a cybersecurity professional, I can attest to the importance of detecting and protecting against crypto mining malware. It’s crucial to monitor system performance, check CPU and GPU usage, and look for unusual network activity to safeguard your devices and networks from these malicious threats.
EmilySmith
27.09.2024 at 17:16
Being aware of the signs of crypto mining malware is crucial in today’s digital landscape. If you experience sudden performance slowdowns or notice unusually high CPU or GPU usage on your devices, it’s essential to investigate further to protect your systems and data from potential harm.
Emily1987
01.10.2024 at 03:18
How can I differentiate between normal high resource usage and crypto mining malware specifically on my device?
Samuel1990
04.10.2024 at 13:37
To differentiate between normal high resource usage and crypto mining malware on your device, you can monitor the CPU and GPU usage levels. If you notice an abnormal spike in usage when you are not running any intensive applications, it could be a sign of crypto mining malware using your device’s resources without your consent.
EmilyCryptoDetective
07.10.2024 at 23:41
Being vigilant about monitoring system performance, checking CPU and GPU usage, and looking for unusual network activity are key steps in detecting and protecting against crypto mining malware. It’s crucial to stay informed and proactive in defending our devices and networks from these cyber threats.
AliceSmith_89
11.10.2024 at 09:47
How can I differentiate between regular software consuming resources and crypto mining malware? Is there any specific software that can help with detection?